This document suggests controls for the physical security of information technology and systems related to information processing.
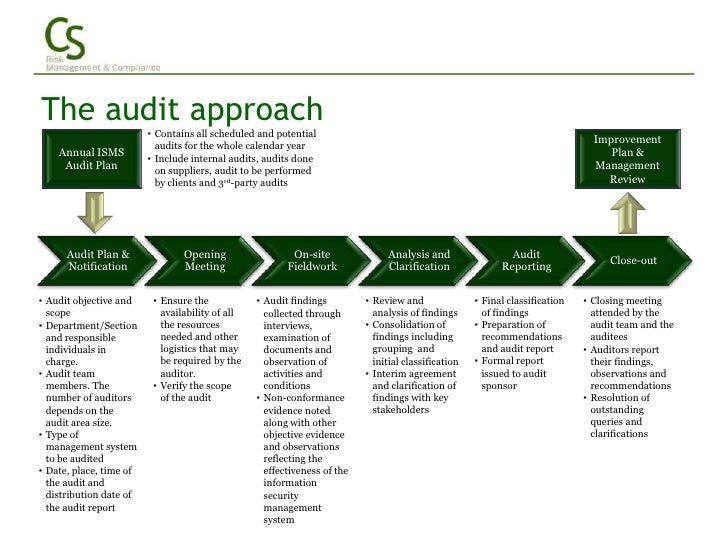
ISMS – AUDIT CHECKLIST Form F252 (ISMS)/Rev 3 (Revised 30 October 2006) Page 1 of 9 REQUIREMENT – REFER TO BS ISO / IEC 27001: 2005 Checked at Stage 1 for development and Stage 2/surveillance for implementation, maintenance and improvement Comment/ Report Ref. Stage 1 Stage 2/ Surv. 4.1 4.2.1 Has the organisation developed a documented. ISO 27001 checklist is useful for carrying out thorough ISO 27001 compliance audit. The ISO 27001 audit Checklist is the ultimate ready reckoner for conducting value added in depth ISMS audit.
1. Introduction
Physical access to information processing and storage areas and their supporting infrastructure (e.g. communications, power, and environmental) must be controlled to prevent, detect, and minimize the effects of unintended access to these areas (e.g., unauthorized information access, or disruption of information processing itself). Access control is established by imposing standards for protection at the building, processing area, and supporting infrastructure areas. The level of control imposed on these areas will reflect the nature of the importance of the information handled or supported by the area to corporate operations. The effects of unwanted intrusion can be painful and costly. If managed properly, physical security policies and procedures can provide the protection that they are designed to give while providing the security that is necessary to keep the resources around it safe from outside threats as well as those from the inside. The purpose of this document is to present the physical security standards as they relate to their strategic use within an organization. Out of this one should be able to follow the information and guidelines to effectively audit the state of a given physical security policy.
2. Building Access Controls
The building access control standards implemented must be commensurate with the type of information processing and the confidentially of information acquired and distributed that is occurring at the physical location. Buildings containing a designated data center will necessarily employ stricter access controls than those that do not. There are also minimum physical access controls, which should be practiced to govern access to all buildings in an effort to protect information resources. The following standards specify the baseline controls for all buildings and additional standards appropriate for buildings that house a data center.
3. Data Center Physical Access

The information processed here is normally deemed critical to operations and is of a sensitive nature in terms of confidentiality issues. Correspondingly, access controls to the data center require a high level of personnel restriction and authentication to safeguard the information processed therein.
4. Supporting Infrastructure Physical Access Controls
Access to facilities that support information processing systems such as the telecommunications room, the emergency power source room (generators, batteries, etc.), the air conditioning unit room and closed areas where network hubs may be stored must be restricted to authorized individuals. Degradation of infrastructure services can jeopardize continuity of information processing and impact operations as a whole. As such, the physical access controls afforded these support systems should reflect the importance of the information processing systems they serve. In most cases, locked doors will suffice to safeguard these support systems. The IT Support Group will implement such physical access controls and will be reviewed and audited by the IT Controls Group and the Internal Audit department.
Iso 27001 Checklist Free
5. End User Portable Laptop Computers Physical Access
Due to the high risk of loss, laptop computers should be traceable to individual users, and sensitive information (to the extent possible) should not be stored on the unit’s permanent disk drive. Portable laptop computers containing sensitive information (non-disclosure) should be protected using a PC security/disk encryption package. All portable laptops must be physically secured via an appropriate security device during any period that the unit is left unattended in the office (normal business hours inclusive).
6. Local Area Networks
Local area networks (LANs) utilized by the business units to accomplish their functions should have the following physical access control standards applied:
• Network servers should be located in a data center which is in an area free from physical dangers (e.g., high traffic areas, water leaks, fire hazards, etc.).
• Access to the servers should be physically restricted to authorized personnel (network administrators) by locating them in a closed area (e.g., a locked office).
• Additionally, unauthorized system access via bypass booting of the server (to defeat password authentication) should be prevented. Software should be scanned for viruses on a separate machine before being loaded on a network server.
7. Employee Termination or Change in Job Responsibility
If an employee has a change in their job responsibility or is terminated for any reason, all of the following items in their possession which control physical access to information must be returned, when applicable. These items include:
Keys to safes and control panels
Keys to cupboard/filing cabinets
Keys to Entrances/doors
Terminal/PCs
Telecommunications equipment
Diskette boxes
Personal Authentication Devices, Secure ID Cards, Random Password Generators
Credit Cards/Charge Cards
Parking Pass/Garage Space
Vehicle
Office/Desk
Uniforms
Company files (hard and soft copies)
Amounts owed to the company
The Supervisor’s Termination Checklist should be used for each occurrence. If keys have not been returned, it may be necessary to replace locks that protect sensitive information. Combination locks should be changed at the discretion of management. It is the responsibility of the employees’ manager along with the Human Resources department to inform the IT Controls Group and other appropriate departments of an employee termination or change in employee job responsibility.
All copyright licensed and business confidential information held on magnetic media as information, programs, operating systems and utilities, must be returned, recorded, and checked.
8. Management of Computing Resources
IT Support and Data Center Groups are responsible for the movement of all types of information system media equipment, and special equipment such as file servers or other related equipment and devices that may reside in any facility or business unit area. The user must not relocate or remove any equipment without the expressed consent of IT Support and Data Center Group.
IT Support and Data Center Groups are responsible for all changes to the network configuration and attached workstations regardless of their physical location, function, application, or use of the network device. To ensure that all networking policies, standards, and procedures are being adhered to, monitoring software may be installed across all LANs and non-company LANs connected to the network.
9. Backup Power for Power Outage Situations
Mainframe and network computer systems and their supporting infrastructure (e.g., air conditioning systems and security alarm systems where applicable) must have a dependable, consistent electrical power supply that is free from surges and interference that could affect operation of the equipment. Backup power is necessary to ensure that computer services are in a constant state of readiness and to help avoid damage to equipment if normal power is lost. A backup Un-interruptible Power Supply (UPS System) must be utilized for the computer systems and supporting equipment. Where appropriate, generators and batteries should also be employed to ensure continuous operations. In areas susceptible to outages of more than 15 to 30 minutes, diesel generators are recommended. Backup power facilities must be regularly tested to ensure reliable functionality.
10. Emergency Power-off Switches
In data centers, emergency power off switches, that shut-off all power supplies, must be installed and be readily accessible with posted notices showing their location. Where justified, the use of these switches must be protected against unauthorized physical access. It is recommended that a power-off switch be located inside and outside of data center rooms.
11. Emergency Lighting
Automatic emergency lighting must be provided in data centers and network server closet areas for use during power outages.
12. Water Sensors and Temperature/Humidity Alarms
The computer environment must be protected from all forms of water, temperature and humidity damage. Locations with the potential for water damage must be avoided when selecting information-processing areas (e.g., locations below ground level, or those under toilets, showers, cafeterias, or similar facilities where water or drainage malfunctions could occur). In data center environments, sensors and alarms must be installed to monitor the environment surrounding the equipment to ensure that air, humidity and cooling water temperatures remain within the levels specified by equipment design. Water sensors must be placed in the floor and ceiling to ensure leakage detection. If proper conditions are not maintained, alarm systems must be configured to summon operations and maintenance personnel to correct the situation before a business interruption occurs.
13. Fire Detection and Suppression Controls
Free Internal Audit Checklist Iso 13485
Measures must be taken to minimize the risks and effects of a fire occurring within the information processing areas, or from spreading into these areas from an adjoining location. The degree of automatic fire detection and suppression mechanisms deployed depends upon the criticality of the operation attributed to the information processing system. Data centers may have halon gas (or approved equivalent) systems or dry pipe sprinkler systems and heat sensors installed, while closed area network server rooms may only have smoke detectors and fire extinguishers. Regardless, fire detection and suppression mechanisms must be utilized in the information processing areas. Where possible, detection devices should notify appropriate personnel.
14. Site Construction Capabilities
Buildings that contain information processing area(s) must minimally conform to local and federal construction regulations especially with regard to natural physical security threats (e.g., fire, flood, earthquake, hurricane, etc.). Selection of new sites should consider the presence of such threats and avoid high-risk conditions where possible. Continual assessment of construction in the area of the facility should be conducted, especially in the case of digging. Many of these issues should be addressed in the company’s Business Continuity Plan.
15. Sign Posting
External signs notices or maps must not identify the information processing area or data center location.
16. Insurance
Insurance coverage should complement an effective system of physical security controls as a countermeasure against threat realization and impact on company operations. The following items should be considered in regards to associated asset values versus insurance cost to mitigate losses.
IS equipment and facilities
Employee fidelity
Media reconstruction
Extra expense
Business interruption
Errors and omissions
Loss of items in transit
Liability to customers resulting from EFT systems activities